If you are taking notes related to an organization’s operations, those notes need to meet certain guidelines of clarity, cohesiveness, and comprehension. To accomplish those guidelines, you will require the correct tools. This entry will appraise two of the industry’s best note-taking applications to help you identify which is best for your needs. The applications: Microsoft OneNote, and EverNote.
Macro Systems Blog
In a statement issued by Tom Bossert, the Homeland Security Adviser to the White House, responsibility for the WannaCry attacks from May 12th to the 15th in 2017 was attributed to the Democratic People’s Republic of Korea. This claim fits with the conclusions that New Zealand, Australia, Canada, and Japan have come to, according to Bossert.
Your company has a solid plan to manage its IT maintenance, or it does not. There is no middle ground. Either your business has an internal team devoted to maintaining your IT infrastructure, or it’s not being taken care of as well as it should be. Even if your organization does have an internal team, you might notice that they don’t have enough time on their hands to handle all of their responsibilities. Let us introduce you to one of the most notable ways of keeping your technology in sufficient working order: managed IT services.
Excel is the primary spreadsheet builder and is tremendously valuable to your business. Spreadsheets are perfect for showcasing information in a compact manner, but without a couple of charts, your users will just be staring at cell after cell of dull old numbers. By using charts in Excel, you can take your spreadsheet building to the next level.
During Christmas, technology is unavoidable. Traditionally, the holidays were a time when things slowed down for companies, people spent time with their families, and business was put on the back burner. Those days are over. The modern professional is lucky to get a day off for Christmas; and, because of the way business works today, may be asked to do more than ever around the holidays.
There are not many security problems that are more dangerous than a network breach. Considering how much you could lose from an unexpected run-in with a hacker, it’s not a surprise that companies are worried. Somehow, even some of the most troubling threats like phishing attacks are often overlooked. A new study introduces the groundbreaking thought that phishing attacks should be at the front of a business owner’s mind regarding network security.

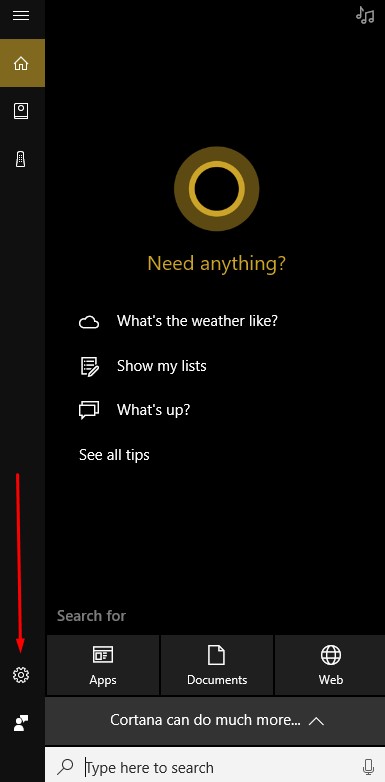
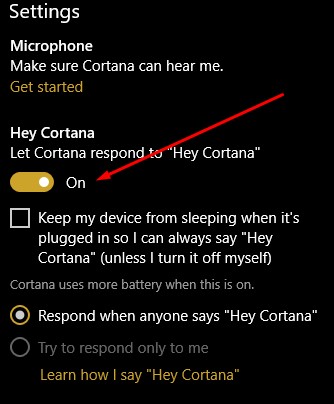
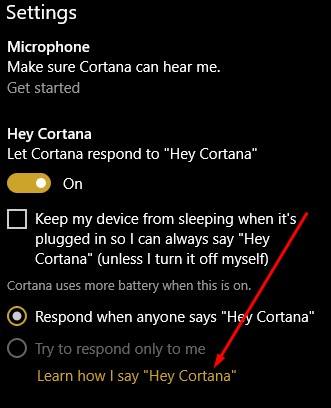
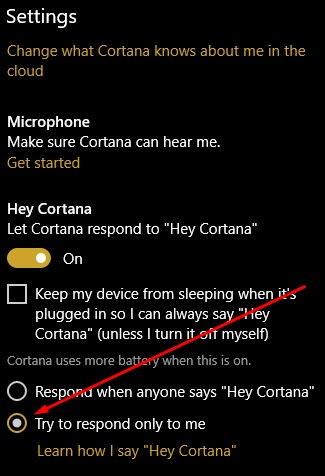
Cortana, Windows 10’s built-in personal assistant, has demonstarted her usefulness for those users who have taken advantage of her services. Occasionally, however, the Cortana interface will answer when another person in the room beckons her. For Cortana to work for one person, and to obey only one voice, the software needs to become familiar with that voice.
Mobile devices have become invavluable in the modern workplace. It'd be difficult to locate a company that doesn’t use smartphones or tablets in some manner. However, mobile devices will never be truly mobile while they need to be tethered to wires plugged into outlets or USB cables due to batteries losing their charges. An innovation called wireless charging has attempted to shake this concept up, but has it proven successful? And what is wireless charging, exactly?
Data security has to be an absolutely critical consideration of the modern business, so every small step you can take to protect your business is important. One such step is the implementation of two-factor authentication. Warning: your employees may not initially feel very comfortable with some facets of two-factor authentication.
Email is such a familiar solution that most people don’t think twice about how it works. However, it’s critical that you at least understand the concept, as it can provide you with a substantial advantage when it comes time to optimize email access on your mobile devices. Let us discuss the ways in which the two major message exchange protocols differ, and then look into the specifics of why you should choose one over the other.
It's reasonable that people may see having a credit card stolen as identity theft, but that is an oversimplification that can prove dangerous. While credit card theft is an element of identity theft, equating the two means that other forms of identity theft are overlooked. Let's go over why identity theft and credit card theft are not the same thing, and what you can do to help keep your business safe.
Insider dangers contribute to a remarkable number of data breaches. These cases of data vulnerability are permitted by a member of your workforce, whether they intended to harm your business or simply made an honest mistake. With so much focus directed toward the dangerss out in the world, sometimes we forget that the biggest threats can be among our ranks. Here are a few ways to keep insider dangers from doing your business significant harm.
The computer an individual owns or uses for work is mostly just a machine used to execute specific tasks. This doesn’t mean that the individual shouldn’t know all of the modern tips that help you get the most out of it, though. Here are some of the best shortcuts that you can use to take full advantage of your workstation.
Collaboration is a critical aspect of business these days, which has led to many developers and providers entering the business of collaboration. These developers are in extensive competition with each other trying to update their offering so it's better than the others. Recently, Facebook Workplace, Slack, and Google’s Gmail each received collaboration-boosting updates.
Black Friday, the day after Thanksgiving, is considered by many to be the beginning of the holiday shopping season. Black Friday is infamous for deals so beneficial that people are willing to wait in line for hours before the stores even open in order to take advantage; however, are these deals really the best compared to Cyber Monday?
The holiday season is nearly here! Filled with lots of gift giving and sharing, you’ll want only the best smartphone to ensure that you can keep in touch with friends, family, and even your clients in case of an emergency. Here are aspects of each major smartphone so that you can make an educated decision about which one you want to purchase.