It's inevitable that employees will bring their mobile devices to work, even if the boss bans them. Instead of worrying about these workers wasting time during the day, try turning those devices to your advantage. There are more tools out there than ever before to not only add smartphones to your workflows, but to make them profitable and valuable for your business.
Macro Systems Blog
Taking into consideration the leaks and vulnerabilities that have been brought to light over the past few years, network security is a critical priority for every organization. One problem many have is that while they are protecting their network and infrastructure from threats outside the business, there are real threats coming from the inside. Below we examine four ways threats can cause havoc from inside your business.
The Internet of Things (IoT) might be a significant upgrade in terms of connectivity for a lot of users and businesses, but this comes at a price. With more devices accessing connected networks than ever before, security becomes a focal point of discussion for the Internet of Things. How can you make sure that your network is secure while these devices run rampant all around your business?
Modern business relies very heavily on IT. As a result, to keep their computing network and infrastructure running efficiently, they need to have a network and cybersecurity policy established. With the development and use of organizational computer networks with multiple endpoints, comprehending the basics of network security is helpful when implementing and employing network security systems. Let's review aspects of your network, their functions, and what you need to do to protect them.
Star Wars is a cultural sensation. For the past 40+ years audiences from all around the globe have become captivated with the story that took place in a galaxy far, far away. However, Star Wars was also a wonderful lesson in modern IT security! Let's examine three situations that happened in Star Wars: A New Hope and, how, if proper IT strategies were implemented, the Empire would have been able to keep its greatest asset protected.
Mobile devices continue to be an important part of doing business, and organizations are ready and willing to accept them into the workplace environment with open arms. Yet, the fact remains that doing so can be of significant risk. Believe it or not, the majority of businesses overwhelmingly support mobile devices, but don’t put measures into place that can protect them in the event of a hacking attack or data leak.
Verizon has taken to publishing a compilation report analyzing data breach statistics with the help of industry partners, a report that is widely regarded as a must-read for the industry. A brief review of the latest edition’s executive summary revealed where information security vulnerabilities lie in industries worldwide and, even more helpfully, what shape those vulnerabilities took. The Data Breach Investigations Report, or DBIR, pulled no punches in outlining what kind of attacks happened in the past year, and how.
There are many types of online threats that the average business owner needs to understand and be prepared for. The problem here is that no two threats are alike, and they all perform different functions. One thing that all threats have in common is that they want to disrupt your operations in any way possible. To help you better prepare your organization for these threats, we’ll discuss a particularly dangerous malware: the rootkit hack.
Mobile devices have many, many uses, all of which allow users to get the most out of them. But what if all of your attempts at locating the best applications just lead to finding a fraudulent app on the Google Play Store? The truth is that the Google Play Store has its share of malware available for download in all kinds of disguises. Let's go over a couple of tips to help you avoid installing them to begin with.
The Internet browser is one of the most used applications for most users on their computer or mobile device. With the flood of aggressive problems, it is very helpful to realize which Internet browser is the best for keeping your data, identity, and network safe. Let's look at the five most popular Internet browsers found on desktop and laptop computers and decide which are the most reliable.
It’s no secret that a data breach can have serious consequences for any business, especially after some of the events that occurred throughout 2017. From the costs to repair any internal damage done to the efforts it takes to regain client trust, recovering from such an attack is no easy feat--and they’re only poised to get worse.
This year could be a significant year for your business; your business needs to be around long enough to see any positives that may come its way, though, which means you need to be prepared for the negatives. Here are four resolutions for you to make this year to help preserve your company’s cybersecurity.
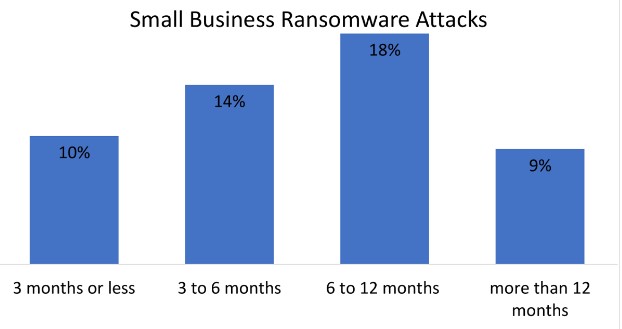
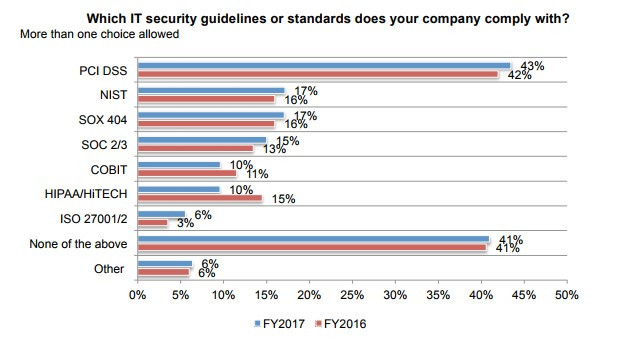
Network security is a crucial consideration for every single organization, especially ones that utilize the Internet. There were a lot of negatives and some positives that came out of 2017 in regards to cybersecurity. Listed below are some of the most troubling cybersecurity statistics collected in 2017, as well as suggestions on how to keep your company safe in 2018.