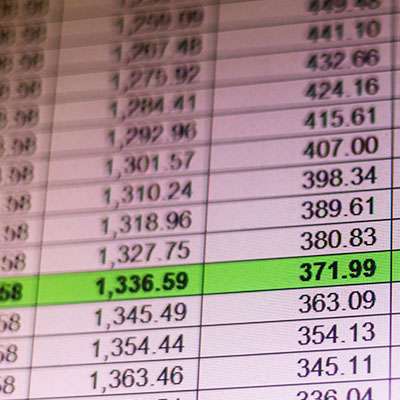
Microsoft Excel is an extremely capable spreadsheet creation and management tool, made all the more powerful via the inclusion of many handy shortcuts and features. We wanted to share one for a common enough function that you are sure to find a use for it: quickly adding up the values in a single column.
Macro Systems Blog
As the boss, you’re in a position to offload many of your business’ responsibilities to your employees. That’s more or less why you have employees in the first place. That being said, there’s more than one way that you can delegate tasks, depending on your personal style of management and the work style of each of your employees.
Businesses use all kinds of sayings to try to draw in customers. One of the core selling points of managed IT services is that “it pays for itself”. This is more than just marketing. The multiple services that make up managed IT services all help a business save time and money, but when added together, it can really help the bottom line of a business more than most services they can use. In this week’s blog we thought we would go through the core elements of a managed IT services agreement to show how it really does pay for itself.
There is a lot of misinformation and misperceptions related to network security out there, especially concerning small businesses. In particular, browser security is one aspect where many individuals’ knowledge simply falls flat, and they buy into myths that put their data at risk. Listed below is an attempt clear up some of these misconceptions so you can go about your day in a more secure way.
Since the Windows 95 operating system, Microsoft has been separately publishing 15 free utilities to add significant capabilities intended to help a user make some small tweaks and adjustments in a relatively safe way, as compared to what would otherwise be necessary to make these changes. Microsoft PowerToys are still available; what some of them can do and how you should go about getting these tools is listed below.
Television has come a long way since its inception, and modern entertainment is more accessible than it has ever been before. Technology has played a large part in the dissemination of this entertainment, so we thought we’d take a look at how the cloud has contributed to making television the cornerstone of leisure that it is today.
If you are like many businesses, you use a lot of services from other companies to try and get all the business computing you need, without having to buy new servers and pay company IT administrators to look after them. This process is understandable, but are you really saving money by doing it? Listed below is a look at the myriad of services that businesses use and if it is, as advertised, saving them money.
We spend a lot of time working with the technology that businesses depend on, including the laptop workstations utilized by just about everyone in many modern organizations. As such, listed below are some of our insights so that you know what qualities you should look for when you’re ready to acquire some additional devices for your organization.
Technology can be expensive to buy and maintain, but it can get a whole lot more expensive if you aren’t cognizant of how your IT dollars are being spent. Long ago are the days when companies could get their technology for a song and it would work for years at a time. Modern business technology has to build a more efficient workplace, as capital is harder to come by today than it has been for quite some time. Listed below are three ways you could be wasting your technology budget and what you can do to ward against it.
The IoT (the Internet of Things) is a fascinating technology, as it exemplifies just how much can be accomplished when Internet connectivity is used to augment the capabilities of otherwise “dumb” devices. Alas, as fascinating as it is, the IoT is also infamous for its security issues, a reputation that attackers have been perpetuating as these devices grow more common.
Data storage is one of those things in business that only is a problem if you don’t have enough of it. It used to be a considerable challenge for businesses, but modern data storage prices are dropping by 20-to-30 percent annually and it has made it feasible for any business to start using cloud computing to store business data. This month we will take a look at the benefits of cloud storage and how there is only one major problem with it.
We’ve been examining the concept of procrastination in recent weeks - why we do it and how it often manifests itself in business processes. For our final few parts, we’ll be focusing on how you can stop procrastinating by utilizing both quicker, short-term tactics and long-term, sustained changes. Listed below are some short-term tactics.
“I just wanted to take a second to thank the sponsor of this video, [insert VPN provider here], for supporting the channel!”
If you’ve been on YouTube in the past few years, this message likely sounds pretty familiar. Virtual private network providers have been taking advantage of the trend of influencer marketing to spread awareness of their largely obscure product, usually offering an enticing deal. While we have and will continue to promote the use of a VPN for business purposes, we wanted to clarify something here: these are not the VPNs we’re saying you should use.
It seems that you can’t turn your head these days without seeing artificial intelligence being incorporated into some software or platform. That being said, many leaders in the technology space have conveyed their concerns about the “profound risks to society and humanity” that AI poses, outlined in an open letter.
We recently started to explore the concept of procrastination as a means of understanding it better, and potentially, getting better at not doing it. Last time, we touched on a few ways that procrastination can potentially manifest, so it only made sense to us that we would continue pulling that thread and try to help you identify how you tend to procrastinate more specifically.