Despite its eccentric name, phishing is a very significant threat to everyone, especially modern businesses. Thus, you must be prepared to identify its warning signs and circumvent risky situations. Listed below are a few tips to prevent you from becoming a phishing victim; make sure you share them with your employees as well!
Macro Systems Blog
Manufacturers are fascinating businesses; not only do they rely on manpower and technology to produce goods, they also depend on IT to power processes, organize their supply chain, and improve organizational efficiency. Since October is Cybersecurity Awareness month we're going to focus on what a manufacturer’s cybersecurity efforts look like.
Many users want to utilize personal devices in a business setting, but some businesses do not support Bring Your Own Device (BYOD) because of the risk of data loss. There are a couple options to separate work data, but not restrict users from their own personal apps or data. Below is a look at how your business can take advantage of employees that already having a capable device, and how you can keep them from compromising security.
The Chromecast is a convenient, easy-to-use device, even in a business setting. Yes, it is a consumer device, but some of its abilities directly translate to professional use. Below is a guide on setting up your Chromecast, four useful-for-business features, and the process of resetting your Chromecast if it ever requires it.
The big tech companies have influence. These organizations, which include Apple, Google, Amazon, and Facebook, have been in the spotlight more and more as the argument of data privacy has increased and become louder. Public sentiment is starting to blow back on their business model--and since, Yahoo, once the principal name in Internet-based services, was broken up and sold to Verizon for cents on the dollar after being at the center of the largest data breach in recorded history--there have been rumblings that there has to be something done to defend the public from major publicly-traded technology organizations that use individual’s data in ways that some deem unethical.
Do you have different passwords for all of your accounts? Are these passwords adequately complex? Chances are you have used a repeating password at some point. Remembering 25 different logins for 25 different applications is hard enough, so it’s not surprising that most people will use the same password for many applications. Bad password practices are all too ordinary. How can you fix this issue?
Thanks to the growing abilities of modern computing networks, businesses have been able to experience increased productivity. One such capability, cloud computing, has permitted businesses to reach outside of their physical location to conduct their operations. Below is a review of some of cloud computing’s other advantages.
No matter how well your new computer operates, you aren’t going to be able to accomplish much with it if you can’t see what you’re doing; you will need a display. Naturally, there are a lot of considerations to make when selecting one, which are outlined below, along with some of the options you’ll come across.
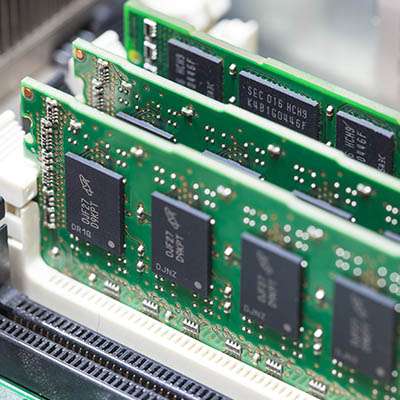
Storage space is the focus of the third part of our computer purchasing guide. As a general rule, modern gadgets have a few available options in terms of storage but the brand and version of the device can have an impact on the amount of space available. As you choose your desktop or laptop to buy, its storage capacity is absolutely imperative.
When you looking to purchase some new computers for your business, making sure that you are targeting the right hardware is critical. To educate people on what they should be looking for in a new computer, we have created a multi-part series detailing the different parts of a computer. In part one, we will take a look at the CPU.
There’s a reason that cybercrime is so common these days: it is no longer reserved for those with substantial programming knowledge to profit from. Now, according to a report by Deloitte entitled Black Market Ecosystem: Estimating the Cost of “Pwnership”, there is a complete economy built around easily accessible hacking tools that don’t require specialized knowledge to be utilized.