Macro Systems Blog
The average business relies on several technology solutions that make maintaining a network infrastructure more challenging. Eventually, it gets to the point where technology becomes difficult to maintain without the help of an on-site IT department. Unfortunately, small businesses often have trouble supporting their infrastructures, as they don’t have the funds to hire and maintain an internal IT department. What’s the best way for a smaller organization to keep their technology in working order?
Tech support has one job: to help you with tech-related problems. Unless it's fraudulent tech support, that is. Many criminals will pretend to be a support tech to gain a target’s trust, with the intention to cause them serious problems. To keep your business safe, make sure that you are able to spot the warning signs of tech support fraud.
Data is the spine of any modern organization. Since your business relies so heavily on it, you need to have measures in place to ensure that your company can access it in some way, shape or form at all times. Easier said than done, especially for a company on a restricted budget. Let's take a look at how you can perform a comprehensive data backup solution to protect your business.
The 28th of January marks Data Privacy Day, which is intended to increase awareness of the significance of data privacy and educate users and business owners of its advantages. Led by the National Cyber Security Alliance, there are numerous lessons the NCSA has to share with organizations as Data Privacy Day places their, and their clients’, privacy in the spotlight.
Similar to other malware, Spyware is a problem for any business. Since your organization generates, collects, and uses considerable amounts of data, there is no lack of other businesses that want to get their hands on it. You spend significant time and money protecting your data against threats on the Internet, but what if the spyware came with the computer you just purchased?
The Internet of Things is somewhat familiar to the world now. IoT devices are in your homes, in your offices, and in your pockets. While these devices are very helpful, they also add to some significant security hazards. Let's review some of the ways to limit these risks while still leveraging the IoT.
How does your organization govern its technology solutions? If you have an in-house IT department, you may think that you have a better opportunity at keeping your organization safe from a hard drive failure, but that is only if your IT department isn’t already flooded with work. You may find that inserting new solutions is difficult, which wastes your time and resources. What is a small business to do?
Connectivity is one of the biggest advantages of mobile technology, but some developments have taken this aspect to wild heights. The Internet of Things is making companies rethink the conventions of connectivity in ways which had not been necessary. Unsurprisingly, the Internet of Things is forcing business owners and others to remain skeptical of connected technology to a certain degree, and a survey from Cisco highlights this trend.
In homes and offices around the world, Technology has become nearly essentially, and one may find themselves replacing it more often than they expected. This leads to a significant amount of waste that can accumulate in your office; whether it's an extra smartphone, desktop, or something as simple as a random, non-functional hard drive. Disposing your dated, unnecessary technology isn’t as easy as placing paper into a recycling bin, however, and it shows in the amount of e-waste that infects the world every day.
Just a few months after the firmware in their computer chips was revealed to be significantly flawed, Intel’s flagship product has yet again resulted in negative attention to the company. While the issue now has a fix, there was the possibility that a solution could reduce the functionality of the CPU.
If there is a problem that everyone is hesitant to address, that problem is called "the elephant in the room". Many businesses may find that, these days, those elephants live in their server rooms. Let's acknowledge these elephants and discuss a few ways that you can evict them from your organization’s IT.
Modern companies rely on so much technology that it’s nearly impossible to think about operations without considering how technology can make them more efficient. Many businesses would completely shut down without the innovations brought about as a result of technology development. One of the most popular trends over the past few years has been the shift from in-house assets to web-based assets, ranging from application access to infrastructure hosting.

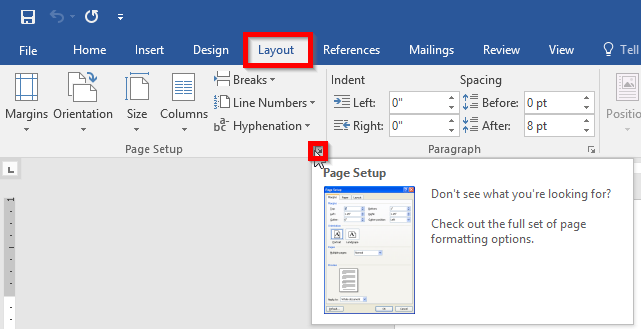
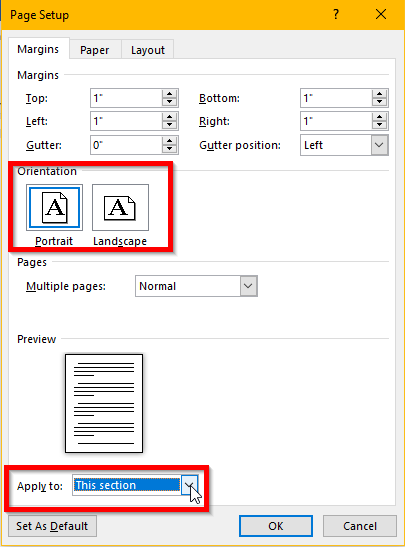
Sometimes using Microsoft Word requires the addition of an outside element, usually something like an Excel sheet, PowerPoint slide or other visual aid. A recurring issue involves having to alter the size of the external element to fit between the margins of the portrait orientation, ultimately subtracting from its impact.
This year could be a significant year for your business; your business needs to be around long enough to see any positives that may come its way, though, which means you need to be prepared for the negatives. Here are four resolutions for you to make this year to help preserve your company’s cybersecurity.
Nearly everyone, at some point in time, has been involved in a situation where personalities clash. This is natural; different people are born with different predispositions and are raised in different environments. Still, in the business world, one should do their best to keep personal differences from affecting their necessary professional relationships.
If you are taking notes related to an organization’s operations, those notes need to meet certain guidelines of clarity, cohesiveness, and comprehension. To accomplish those guidelines, you will require the correct tools. This entry will appraise two of the industry’s best note-taking applications to help you identify which is best for your needs. The applications: Microsoft OneNote, and EverNote.