There are not many security problems that are more dangerous than a network breach. Considering how much you could lose from an unexpected run-in with a hacker, it’s not a surprise that companies are worried. Somehow, even some of the most troubling threats like phishing attacks are often overlooked. A new study introduces the groundbreaking thought that phishing attacks should be at the front of a business owner’s mind regarding network security.
Macro Systems Blog
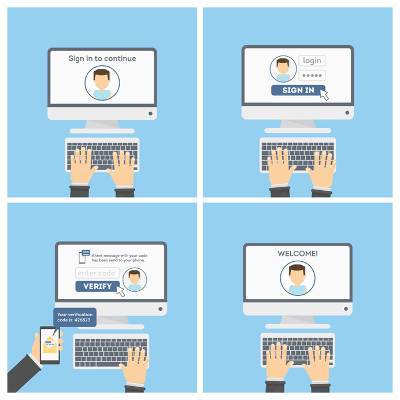
Data security has to be an absolutely critical consideration of the modern business, so every small step you can take to protect your business is important. One such step is the implementation of two-factor authentication. Warning: your employees may not initially feel very comfortable with some facets of two-factor authentication.
It's reasonable that people may see having a credit card stolen as identity theft, but that is an oversimplification that can prove dangerous. While credit card theft is an element of identity theft, equating the two means that other forms of identity theft are overlooked. Let's go over why identity theft and credit card theft are not the same thing, and what you can do to help keep your business safe.
Insider dangers contribute to a remarkable number of data breaches. These cases of data vulnerability are permitted by a member of your workforce, whether they intended to harm your business or simply made an honest mistake. With so much focus directed toward the dangerss out in the world, sometimes we forget that the biggest threats can be among our ranks. Here are a few ways to keep insider dangers from doing your business significant harm.
The capability to vote is one of the most significant rights in the world, setting an individual's voice and opinion into action to shape history. However, it has been demonstrated that the electronic voting machines that some states in the United States use just are nowhere near secure enough to ensure that the democratic process is preserved.
There are numerous businesses in the world that straight-up can’t have hackers and cyber criminals interfering with their data. One of these organizations, CERN (whose acronym translates to the European Laboratory for Particle Physics) has far too powerful of a computer grid to allow hackers to access it. To keep it safe, CERN has deployed what may be the future of cybersecurity: artificial intelligence (AI).
A significant number of security risks come from the interior of your business. User error on the part of the employee can bring serious issuess for your workflow, data security, and the integrity of your organization. User error could be as simple as an employee clicking on the wrong links when they receive a suspicious email in their inbox, or if they are accessing data that they simply have no business accessing in the first place. There are even situations where organizations completely forget to remove employee credentials when they depart the company, resulting in a vulnerable opening in your network. The bottom line is that user error must be accounted for.
There are numerous surveys and reports produced each year that evaluate digital threats and cybercrime. Not every publication applies to every business - but many of them do have some important take aways regarding the best practices of handling IT. Here’s few highlights from the 2017 Cyberthreat Defense Report that offer important insight for SMBs and their use of technology.
If you’ve watched the news lately, you may have seen the Equifax breach and the absurd fallout it has caused. Over 133 million personal records have been stolen. While it’s difficult not to feel individually victimized by such a breach, it’s vital to realize that it’s usually not your specific credentials targeted by cyber criminals. Since businesses often hold onto valuable information, they have large targets planted onto them. It doesn’t stop there--any vendors or partners you deal with are also in danger of cyber attacks.
In the last few months, there have been several high-profile data security breaches that led to the theft of millions upon millions of non-public information records. Though much of the focus in the aftermath of the breaches was on personal identity theft and prevention, it’s imperative to keep in mind that not all the stolen data records target individuals. Organization entities are also at risk. Vendors and partners that you do business with regularly will probably have record of your company’s non-public information, payment information, or tax ID number.
The 2016 United States presidential election was an ugly one for several reasons, including the accusation that hacked voting machines could have altered the outcome of the election significantly. Fortunately, there are steps being taken to alleviate the worries that third parties might alter the outcome of such important events.
Most small businesses lack the luxury of an in-house IT department. Even if they do have one, it’s likely a small department run by a few people who have are busy with either implementation projects or simply keeping up with the status quo. With opportunities to invest in the improvement of your infrastructure few and far between, a network audit can make you aware of where your network suffers most, and what you can do about it.
In February of 2016, President Barack Obama passed a Cybersecurity National Action Plan. The plan performed near-term actions and developed a long-term game plan to intensify cybersecurity awareness and protections, protect privacy, and preserve public safety. Taking action against cybersecurity now will assist with ensuring economic and national security, as well as empowering Americans to take better control of their digital security.
Chances are, you’ve heard of spam, but many don’t know how to identify it in the first place, let alone work around it. Frankly, spam can cause some serious damage to your business if not properly dealt with. In today’s blog, you’ll learn what makes spam, “spam,” and how you can keep it from infecting your inbox.
Over the past several months, while watching the news or reading about business and technology, you’ve probably encountered a few words, such as ‘ransomware’ ‘exploit weakness’, and ‘security patch’. These terms are used often, and you may be confused as to what they really mean, and how they relate to you and the security of your business’ data.
It goes without saying that businesses that don’t want to invest in the latest and greatest software solutions will be denying themselves the opportunity for more productivity and efficiency, but most of all, security will be put on the line. A new study has proven that there is a direct correlation between businesses that run older versions of out-of-date operating systems and web browsers, and organizations that suffer from data breaches.
It doesn’t matter which industry your organization falls into. Your business will always be susceptible to threats in some way, shape, or form. Therefore, it’s your responsibility to ensure that your business understands how to protect itself from these threats, before it’s too late. We’ll help you learn more about the various issues that you need to watch out for, and what you can do to stop them.
The Internet of Things is all around us, in our homes, our offices, and even our cars. While this connectivity can provide a more unified and automated approach to daily tasks, it has the downside of enabling certain security threats to go unfettered. A prime example are the IoT-driven botnets that seem to be increasing in popularity.