“It won’t happen to me.” This is a common excuse amongst business owners who refuse to equip their network with a comprehensive data backup and recovery solution. They may feel like they’re careful enough to avoid a major data loss-causing disaster. Yet, the inconvenient fact remains that a disaster can happen to any business, no matter how prepared they may be.
Macro Systems Blog
No matter how well you protect your network, chances are you’ll suffer eventually from some vulnerability or another. However, you can take considerable measures toward protecting your business so you don’t have to worry so much about it. Listed below is how your efforts today can protect your business now and in the future.
Mobile devices have become a vital part of our daily lives, to the point that many of us openly feel undressed without our phones. As a result, our phones go everywhere with us. On the other hand, it’s imperative to remember that some applications have requested access to our location information. Do all of these apps need to know precisely where we are?
Chances are, you’ve gone through some old files, deleting what is no longer required. This is especially critical when you are upgrading your storage and getting rid of your existing storage media or an old computer. Let’s talk about what really happens when you’re doing so—chances are, you may be overlooking a serious security problem.
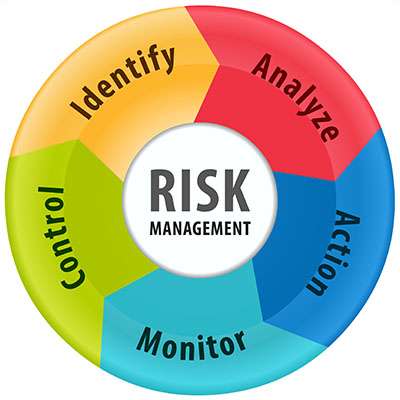
Macro System has been known to take a bit of an extreme approach to cybersecurity—your business is at constant threat of being attacked by all manners of threats and all that. While we stand by this approach as an effective way to enhance awareness and adherence to cybersecurity needs, there are certain attacks that are more likely to target you. This is where risk management comes into play.
It’s almost summer, which means baseball is in full swing. The sport that many of us grew up on has recently gone through a major shift, one which small business owners can replicate to help their organizations. It came about via the use of data and today we’ll discuss how the national pastime has changed and how you can use the same strategies to help make your business better.
Data breaches—any event where an organization's confidential data is viewed, copied, or stolen by an unauthorized person or party—are a serious problem. Alas, they are also a serious problem that can be caused by no shortage of situations. Listed below are some of the causes of business data breaches so you’ll know what to keep an eye out for.
March 31st is the official World Backup Day, a day intended to remind us all of the importance of having backups for the sake of data continuity. While this kind of day can be a valuable reminder of an imperative best practice, we contend that your awareness of your backup, as well as the maintenance that goes with it, should not be limited to a single day.
Cybersecurity is an important subject for a business’ entire team to appreciate, particularly when it comes to the minute differences between different terms. For instance, a layperson might hear “breach” and automatically think “security incident.” While this technically isn’t incorrect, per se, the two terms aren’t really synonymous.
Let’s take a few moments to dive into the minutiae and define these two terms more clearly.
Healthcare is an industry that operates under very high pressure for a significant share of the time. As a result, it is only natural to conclude that a technology that could make the lives of healthcare providers and administrators easier in numerous ways shows some promise. That technology? Artificial intelligence.
Listed below is a few of the many ways that AI has been proposed (if not implemented already) as a solution to some of healthcare’s more challenging obstacles.
We are fans of the cloud, especially for data storage, but you shouldn’t implement the cloud without a good security strategy. Whether you are using it for your organization's data storage needs or just to take backups of your infrastructure, you’ll still need to keep various facets of security in mind for your cloud storage. It all starts with figuring out how secure your cloud provider really is.
Keeping your data protected is a colossal concern these days, with more and more safeguards needed to prevent it from being exfiltrated. Encryption is a great way to keep your data from being any good to those who might steal it. Listed below is an explanation about what encryption is, and how it works in practice.
Whether you refer to them as customers or clients, the people who act as patrons to your business are essential to its success and survival; you need to keep them as happy as possible. While there are many aspects of maintaining a high level of customer service, we wanted to take a bit of time to examine how deploying the right technology can assist your business in doing just that.
While we cannot express how critical it is to update your software and hardware in a timely fashion, it is imperative to keep in mind that some of these updates aren’t going to be perfect. An upcoming update to Google Workspace serves as the perfect example, as the company has recently released an alert to inform users about an issue affecting Google Drive.
The last few months have been filled with severe cyberattacks, particularly those taking advantage of major businesses that might not initially be considered targets for these kinds of attacks. For example, McDonald’s Restaurants was recently breached. We examine the situation below, and how it plays into the recent trends we’ve witnessed.
The blockchain has made quite an impact, beginning as the technology that powers Bitcoin before branching out into different use cases that many businesses are already taking advantage of. Listed below are the benefits and shortcomings of the numerous varieties that blockchain now comes in, and how they are commonly utilized.