Digital communication is a critical part of running any business, so you need to do your part by equipping your employees with the tools they need to communicate effectively both in and out of the workplace. Listed below are three of the most effective tools that will enable your business to flourish.
Macro Systems Blog
With so many employees working remotely, it’s imperative that you do all you can to ensure they have set themselves up for success with their home office. To this end, we have put together a list of suggestions you can use to help your employees build the most comfortable, and productive, home office possible. Here are four tips you can implement for a more comfortable workplace.
You may or may not have already made the transition back to the office, and this especially applies more to those who haven’t yet. That being said, even those who have may find some utility here, specifically in determining if a push to a full return to office was the right move.
Let’s explore how modern employees may react to the news that remote work will no longer be an option.
Technology is one part of your business where you would rather take proactive measures than react to problems that arise. After all, preventing some of the disasters and problems which surface could save you so much time and resources. Listed below are five of the best reasons why you should take a proactive approach to your business’ technology infrastructure.
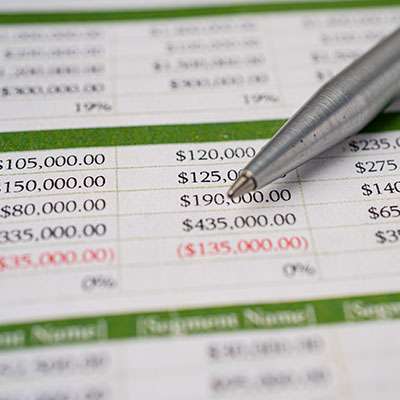
Microsoft Excel is a valuable tool that offers lots of value to power users, but oftentimes users just don’t have the knowledge to make the most of it. Fortunately, you have power users like us to guide you through some of the more intricate processes in the spreadsheet software. Listed below is a look at one such process: removing duplicate values in columns.
Modern Businesses have to deal with more potential problems than in any time in history. These problems include cost increases at every turn, personnel shortages, and a regulatory landscape that is always evolving. One of the biggest issues that can have a negative effect on a business is not having the processes and resources in place and working to secure its data and network. Listed below is a look at five suggestions that can work to help your business keep its network and data more secure.
Security is an incredibly critical part of running a business, but it’s extremely easy for busy employees to fall short of the security expectations you might place on them. This is why it is so imperative to train your employees on the many facets of cybersecurity. By training them, you are preparing them to tackle the variety of challenges they will encounter throughout the workday.
If you want to limit costs, being proactive can go a long way toward this goal. Your organization's technology is one such area where proactive maintenance can allow your business to save countless dollars and hours of downtime. If you haven’t implemented a proactive maintenance platform yet, then you might be putting your business at risk.
It’s almost summer, which means baseball is in full swing. The sport that many of us grew up on has recently gone through a major shift, one which small business owners can replicate to help their organizations. It came about via the use of data and today we’ll discuss how the national pastime has changed and how you can use the same strategies to help make your business better.
Being a manager is a far different experience than being an employee. So, when you promote one of your team members to this position—or perhaps you’ve recently been promoted to management yourself—it is critical that a few practices are incorporated into their new workflow. Let’s go over these practices, and how the right IT can help.
The workspace is consistently changing these days, with remote work being commonplace, along with resignations in the face of a return to the office becoming more of a regular occurrence. Employees want more control over their work schedule so they can balance their personal responsibilities with their professional. A shorter workweek might be the key to making this happen.
Every organization wants to make smart technology decisions. For the small business looking to get their workforce the affordable workstations one modern option that you have is utilizing the budget Chromebooks that are available. Listed below is a discussion about what the Chromebook can bring to your organization and how it can help you reduce your hardware costs and get your staff the resources they need to be productive.
There are many ways that you can invest in your business. You can hire more people with a strategy to get more done; you can diversify and try to cultivate different types of revenue; and you revitalize your business via the use of technology. Below is a discussion on how deploying certain technologies can help grow your business fast.
Technology enables some amazing things for businesses, but it can influence the way you both look at operations and the way your business functions. Not all companies have the capital to make these large technology investments. You are far from optionless, however; listed below are some of the better investments you can make in your technology infrastructure, in particular ones that won’t drain your budget.
Due to the increasing complexity and rapid growth of the cybersecurity industry, businesses must stay ahead of developing threats designed to undermine advancements in the latest and greatest security technologies. One way that researchers have used to fight against threats is through the use of artificial intelligence. It’s possible that this emerging technology could be the key to fighting back against cyberattacks.
How many security solutions does your business have implemented at any given time? Traditionally, businesses have implemented what we call “point solutions,” which are software tools designed to address a specific part of your security infrastructure. While this approach is better than not having security at all, it presents several issues that must also be addressed in order to most effectively protect your business.
Maintaining your organization's technology can be a lot to handle, especially if you don’t have any IT staff members on hand to dedicate to its management. Managed services make this process a lot simpler, ensuring that, amongst other key benefits, your desktop solutions remain up-to-date and prepared for anything. Listed below are three basic tips to follow to ensure your desktops remain maintained.
One of the fastest-growing services in healthcare is telehealth. If you aren’t familiar with this concept, it is essentially a virtual meeting designed to provide faster and more direct healthcare consultations and stabilize the ever-rising costs of healthcare. With health information being one of the most attractive to hackers, it is imperative to be mindful to do everything you can to protect your data. Listed below are four tips to help you successfully navigate the risks inherent with telehealth.