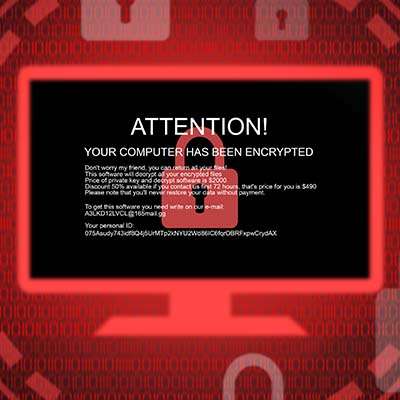
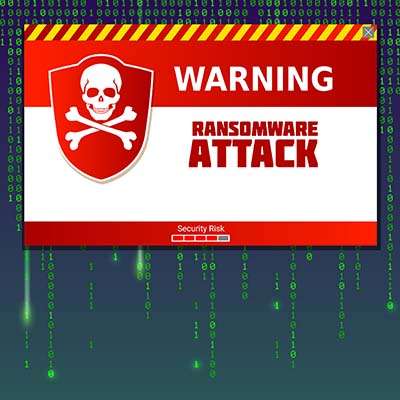
Cybersecurity is an important subject for a business’ entire team to appreciate, particularly when it comes to the minute differences between different terms. For instance, a layperson might hear “breach” and automatically think “security incident.” While this technically isn’t incorrect, per se, the two terms aren’t really synonymous.
Let’s take a few moments to dive into the minutiae and define these two terms more clearly.