Unless you’ve been living in the wilderness for the past couple of decades, you’ve heard of Facebook, Twitter (now X), and Instagram. Most people have some sort of social media presence on one or all of these platforms (or at least on LinkedIn, TikTok, or YouTube). Many businesses once utilized or currently utilize these platforms as a part of their marketing efforts, and despite being billion-dollar companies, there are some grave concerns about the viability of these platforms going forward. Below is a discussion about some of the issues people are having with these established social media platforms and how alternatives might just be the future of social media.
Macro Systems Blog
Did you know that phishing is the most common security risk to your business? Any of your employees could become the target of a phishing attack, and all it would take is downloading the wrong file or clicking on the wrong link to expose your organization to security threats. Listed below is a refresher on the throwaway signs of a phishing attack and how to protect yourself and your team from harm.
Net neutrality has long been an embattled topic, with rules changing every few years depending on the opinions of those with influence. Recently, the Federal Communications Commission had its most recent net neutrality policy struck down by the 6th Circuit Court of Appeals… in such a way that sets the concept back to square one.
Listed below: why this is a particularly dangerous decision, and very well could put small and medium-sized businesses at a distinct disadvantage moving forward.
For years, the telephone has been one of the most reliable business communications solutions, and that trend will continue into 2025. If you’re still using the phone solutions of the past, however, you’ve got some upgrading to do. Listed below is what you need to know about the best communications investment you can make: Voice over Internet Protocol, or VoIP.
Many market analysts and industry experts foresee an increase in the cost of hardware. We recommend that you take matters into your own hands to avoid the price hike and buy your new IT now before it costs you more to do so. The implementation of any proposed tariffs could impact the market as early as February 2025, so we wanted to discuss what you should consider when purchasing new hardware today.
Your smartphone is probably one of the most critical tools in your daily life; it helps you stay connected, entertained, and organized. But smartphones aren’t cheap, and replacing one every couple of years can hurt your wallet. The good news? With a little care, you can make your phone last longer. Listed below are five easy tips to keep your smartphone running like new.
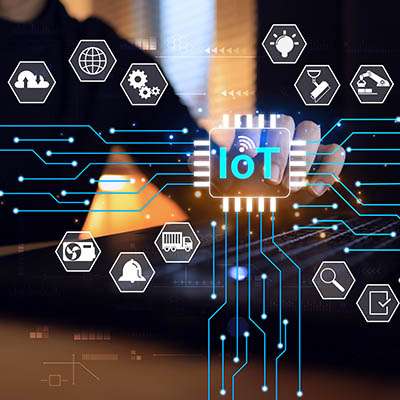
The Internet of Things (IoT) is a fascinating technology that can help businesses. When used in offices, it changes how things are done, bringing benefits such as increased efficiency, better productivity, and enhanced security. IoT devices and systems make tasks easier and create a more comfortable, eco-friendly, and productive workplace. Listed below is how small businesses can use IoT to improve how they operate.
Remote work isn’t a new strategy, but ever since the COVID-19 pandemic shut down in-office activities for all types of businesses, the amount of remote workers has grown regularly. In 2024, nearly 22 million workers would be considered fully remote, with over twice that amount working a hybrid schedule where they are remote at least one day per work week. This shift in the way that people work has required some adjustments, and this month, we wanted to take a closer look at the employees’ side of the “new normal”
To be clear, this won’t be a comprehensive list of problems that remote workers are dealing with, but we will try to go through some of the challenges and benefits that people deal with when they work remotely.
Want more productivity from the workday? Multiple monitors can help you achieve this goal. You might run into the problem of “ghost monitors,” though, where your PC believes you are connected to screens when you’re not. If you experience this problem and your application windows are off-screen and unobtainable, you’ll find this week’s tip helpful.
With the price of hardware at risk of skyrocketing, it’s no wonder that many businesses are looking to virtualize as much of their operations as possible. This is where the cloud comes in: you can virtualize just about any solution, including some that you might not have considered in the past. Listed below: how an SMB might use virtualization and cloud computing to skirt hardware acquisition costs.
Do you ever feel at home in your business’ server room? Assuming you have a server room, and it’s more than just a stuffy closet in an isolated part of your office, that is. If you’re not confident that you can provide your servers with the management, maintenance, and monitoring they require, we recommend you work with a managed IT company to ensure you get the most value you can from your server units.
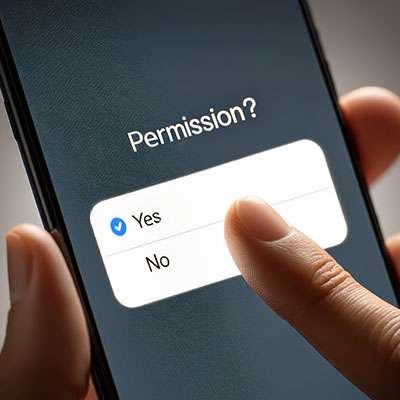
Your Android device provides a lot of capabilities in its little frame, with many people relying on theirs to keep their lives organized. Many businesses even rely on Android mobile devices. This should only reinforce how imperative privacy and security are.
In light of this, listed below are a few simple tips anyone can do to help make a smartphone that much more secure.
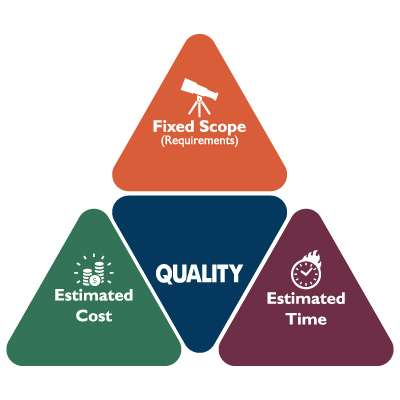
There is a concept known as the iron triangle that offers a simple framework for project management by outlining the balance between your costs, your available time, and the desired quality of your outcome.
Traditionally, the iron triangle helps illustrate how these factors impact each other. Instead, we wanted to take advantage of the principles of the triangle to explore how advantageous it can be to outsource IT services.
The big thing in business computing is AI, or artificial intelligence, and businesses are implementing it to solve a lot of repetitive issues that free up their employees to serve other roles. One such area is for IT support. But is it worth it to chat with a robot when something as imperative as IT is on the line?
While we all know how much magic the workshops up at the North Pole depend on to produce presents for the good children of the world, we have it on good authority that they also depend heavily on technology. For example, there are a lot of letters that need to be sorted and read before Santa’s big ride. Let’s read up on what our partners up north frequently deal with in their critical operations.
If you want your business to succeed, you need to take care of your employees, but businesses sometimes let this imperative task slip in the throes of the day-to-day. Deloitte estimates that around 8 out of every 10 wage workers show signs of burnout. So the question then becomes: What are you doing about it?